
Is your business prepared for a ransomware attack? Small businesses are not immune to the risk, so it’s wise to operate with an “assume breach” mentality. That’s why knowing how to respond to an attack is equally important to helping prevent one.
The 2022 SonicWall Cyber Threat Report reports ransomware volume in the U.S. rose 98% between 2020 and 2021 to 421.5 million attempts. The number of attempts is not projected to slow down any time soon.
Plus, ironically, the very tools that allow us to work remotely can also make us more casual about security, which increases the risk of an attack.
Preparation and Planning
It’s important to adjust your thinking from focusing only on how to prevent a ransomware attack. Give equal attention to achieving confidence in how you will respond when the attack happens. Your investment in planning for recovery could make or break the future of your organization.
A good place to start is the NIST Cybersecurity Framework. The NIST framework is one of the most widely-accepted tools for cybersecurity planning and response.
There are five key components to the framework: Identify, Protect, Detect, Respond and Recover. Your IT provider should have tools and processes in place that address each of the five components.
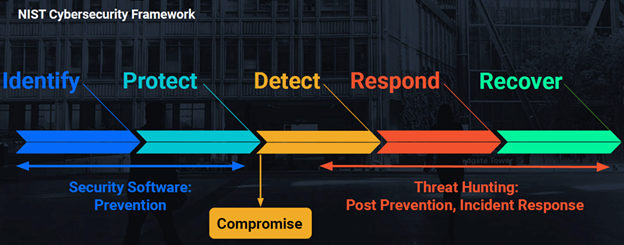
Graphic: Huntress
Work with your IT provider as you develop your plan. While it requires some thought, it doesn’t have to be overly arduous. The time you spend up front will put you in a strong position to recover more quickly when an attack occurs.
We’ll focus on an overview of the Identify and Protect steps in this post.
Identify
Here are a few questions to consider that will help you understand what you have and where there are vulnerabilities:
- What data do you have? Who has access to it? How does it flow?
- What hardware and software do you use? Who uses which machines?
- Are you using current software versions? Are your systems regularly patched?
- What are the internal and external vulnerabilities and risks to your IT assets?
- What does it cost for each day you can’t access your systems? How much downtime is tolerable?
- If you had to completely shut down the network for a week to remediate, how would you operate your business during that time?
- After a compromise, what critical processes need to be restored first? What services need to remain operational no matter what?
- If you lost sensitive customer information, what process would you follow to investigate the extent of the loss and how would you disclose this to your customers?
Answers to these questions and others will help determine how you should protect your current environment and position yourself for successful recovery.
Protect
Protection requires a layered approach that includes tech tools and staff training. New risks appear daily, so no solution is 100% fool-proof against ransomware. Still, there are concrete steps you can and should take. Here are just a few:
Use multi-factor authentication. As recently as a few years ago, using multi-factor authentication on every account was considered useful but optional. Today, it’s essential to significantly reduce risks.
Use a password manager. It’s estimated that the average person has 100 passwords or more. A secure password manager keeps track of them all. You only need to remember one master password.
Apply software patches to improve security, minimize downtime, and meet compliance requirements. Patches often include new software features as well. Your IT provider can provide patch management and reporting.
Use encryption on machines and for sensitive email. Encryption can be a roadblock for cybercriminals by simply making your data more difficult to access. Also use encrypted email if you must transmit sensitive data.
Require regular cybersecurity awareness training for all employees. The person sitting at the keyboard is usually the last line of defense for an attack, so every computer user is responsible for cybersecurity. Simulated phishing testing and short online training offer great reminders to be careful. Also develop policies and procedures that emphasize cybersecurity.
A reliable, quickly recoverable backup is essential to help speed up and smooth the recovery process after an attack. Backup as a Service that includes both onsite and cloud replication can get you up and running faster. Remember to backup workstations as well. Even if you save all your files to the server, there’s still more on your local computer than you may realize.
Cyberliability insurance is no longer a “nice to have”. Talk with your insurance company to determine what type of policy is best for your organization. The right cyberliability insurance could be critical to your recovery.
Detect, Respond, Recover
After a compromise is detected, rely on your IT team to have the proper tools and skills in place to support you in response and recovery. As part of your planning, create action steps including how you’ll stay in touch with your staff, clients and other stakeholders while the IT team is hard at work on the technical side. You’ll likely need help from your attorneys, communications team, insurance providers, and possibly law enforcement.
Our Perspective
While news reports usually focus on the technology behind ransomware attacks, don’t underestimate the emotional impacts. The first hours and days will be stressful. There may be long term effects as well, which can take a toll.
Still, your preparation will put you in an excellent position to fight off the fear and return to “business as usual” as soon as possible.
Does this sound like overkill for a small business? When the attack happens, your planning will pay off. Work with an IT provider who has the experience, tools, and knowledge to benefit your business. That confidence should help you sleep better at night.
If you’d like to know more about how CRU Solutions can help keep your business safer, contact us.